Mobile Device Security – Tips and Tricks for General Users

Mobile Device Security – Tips and Tricks for General Users: a post in a series of articles for general endusers to better protect themselves online. In today’s world, our mobile devices have become an integral part of our daily lives. They store our personal information, allow us access to our finances and healthcare information, help […]
Online Identity – Protecting yourself from Theft

In this digital age, protecting your online identity is essential. Cyber criminals are constantly on the lookout for ways to hack into your accounts and steal your sensitive information. One of the best ways to enhance your cybersecurity is to use strong, unique passwords for each of your online accounts and enable two-factor authentication (2FA) […]
Protecting yourself Online: A Beginner’s Guide for Information Security
In today’s digital age, information security is more important than ever. With cyber threats on the rise, it is crucial for everyday users to understand the basics of protecting their personal data. In this article, we will discuss key principles, strategies, and best practices to help you strengthen your online security. By the end of […]
Risk Management or how high is that cliff?

Risk management is an indispensable element of cybersecurity for any organization. As the complexity and frequency of cyber threats continue to rise, implementing effective risk management practices becomes vital in protecting sensitive information, ensuring business continuity, and preserving an organization’s reputation. In this post, we will delve into the roles and responsibilities of various stakeholders […]
ChatGPT-4: not always what you ask

Shall we play a game? In my continuing saga of messing around with OpenAI‘s ChatGPT-4’s Artificial Intelligence (AI) Large Language Model (LLM), I have noticed that its not always what you ask it, but rather how you phrase your questions ChatGPT-4 rightly has a number of safeguards in place to prevent it from providing information […]
Information Security Training: Why & How

Empowering Your Workforce to Safeguard Your Organization’s Digital Assets Introduction In today’s regulatory, litigious and online world, information security is a top priority for businesses of all sizes. With the increased reliance on technology and remote work, the potential for cyber threats is higher than ever. It is critical for organizations to invest in information […]
ChatGPT 4.0 – more blogging via Artificial Intelligence
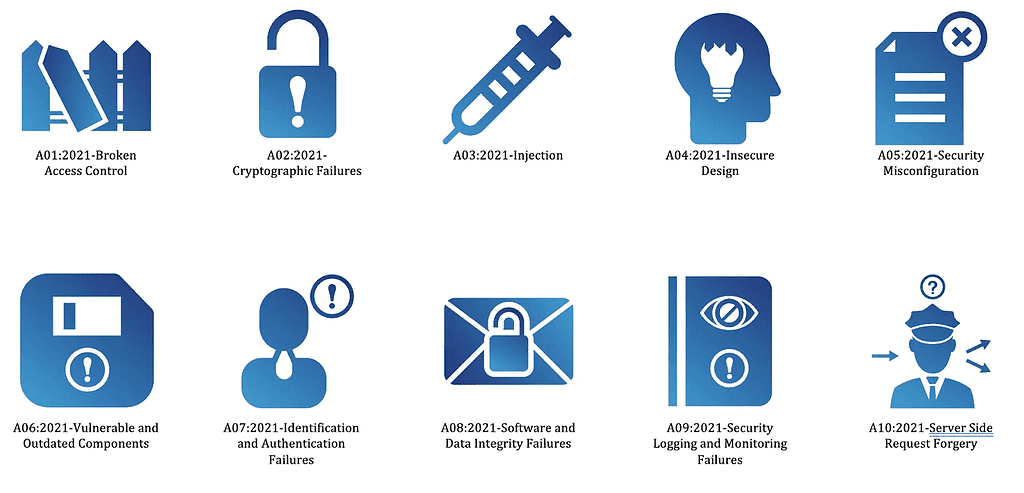
[Author’s Note] The following was part of my testing of artificial intelligence (specifically ChatGPT’s) ability to write technical blog posts and also create training materials for developers to better understand secure coding practices. I used ChatGPT 4.0 for this and may go back and refine the prompts I used to get more complex examples, but […]
Security and the (in)Human Element

This weekend a friend of mine was caught by yet another Facebook social engineering security event. It was a run of the mill phishing attack, and his credentials were compromised and scores of messages were sent out. The messages were simple “It’s you in this video?” with a fake link to Youtube (see image). This […]
Home Automation Solution Mapping
Home Automation, or has my house become self-aware? SkyNet Be Damned! I’ve been playing around with Home Automation and SmartHome IoT technology for a couple of months and went searching for a way to map out all the connections, dependencies and devices in the house. I tripped across SmartHomeDB on my twitter feed and gave […]
WannaCry in my beer
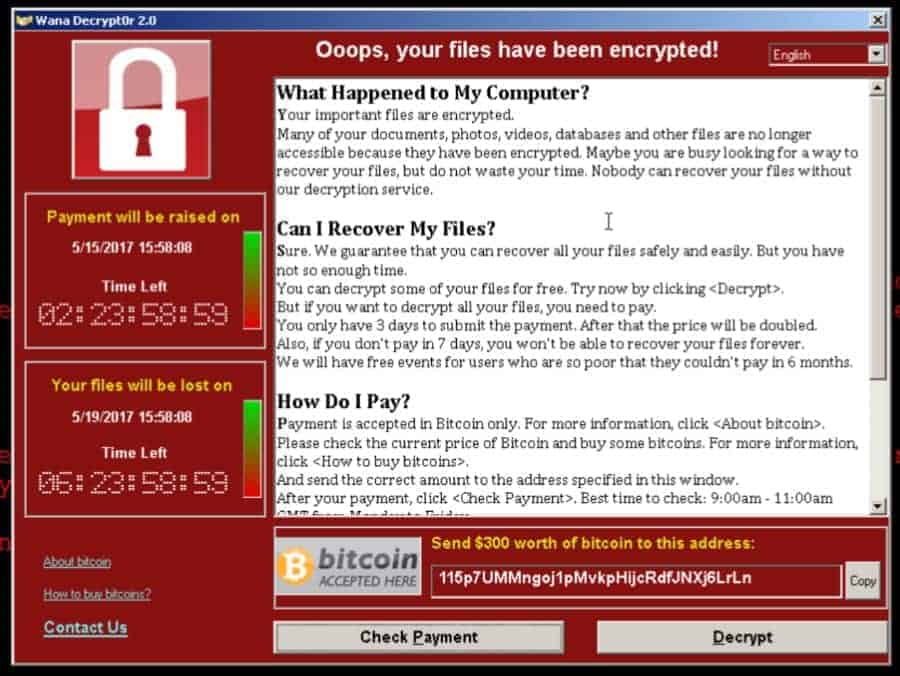
WannaCry or the Cyber-Event that should never have happened Ok, the WannaCry tears are drying and InfoSec and IT professionals around the world are catching up on sleep lost over the weekend. A fair number of them are probably, like me, wondering how this became so ugly and so widespread. While I know this cyber event had […]

