Home Lab Environment for Security Testing

Why Build a Home Lab for Security Testing? In the Cyber Security field, theoretical and book knowledge pales in comparison to the insight gained from hands-on experience and doing the thing. This article kicks off a series dedicated to those wanting to get started in this field, or those who are already working in the field […]
Online Identity – Protecting yourself from Theft

In this digital age, protecting your online identity is essential. Cyber criminals are constantly on the lookout for ways to hack into your accounts and steal your sensitive information. One of the best ways to enhance your cybersecurity is to use strong, unique passwords for each of your online accounts and enable two-factor authentication (2FA) […]
Protecting yourself Online: A Beginner’s Guide for Information Security
In today’s digital age, information security is more important than ever. With cyber threats on the rise, it is crucial for everyday users to understand the basics of protecting their personal data. In this article, we will discuss key principles, strategies, and best practices to help you strengthen your online security. By the end of […]
Ransomware Detection & Response

Ransomware attacks have been on the rise in recent years, causing significant financial and operational disruptions for organizations across various sectors. This brief guide covers essential ransomware defense strategies, including understanding what ransomware is, implementing technology solutions and process controls, and preparing your organization to respond effectively to a ransomware attack. Ultimately, some of these […]
Risk Management or how high is that cliff?

Risk management is an indispensable element of cybersecurity for any organization. As the complexity and frequency of cyber threats continue to rise, implementing effective risk management practices becomes vital in protecting sensitive information, ensuring business continuity, and preserving an organization’s reputation. In this post, we will delve into the roles and responsibilities of various stakeholders […]
Information Security Training: Why & How

Empowering Your Workforce to Safeguard Your Organization’s Digital Assets Introduction In today’s regulatory, litigious and online world, information security is a top priority for businesses of all sizes. With the increased reliance on technology and remote work, the potential for cyber threats is higher than ever. It is critical for organizations to invest in information […]
Security and the (in)Human Element

This weekend a friend of mine was caught by yet another Facebook social engineering security event. It was a run of the mill phishing attack, and his credentials were compromised and scores of messages were sent out. The messages were simple “It’s you in this video?” with a fake link to Youtube (see image). This […]
WannaCry in my beer
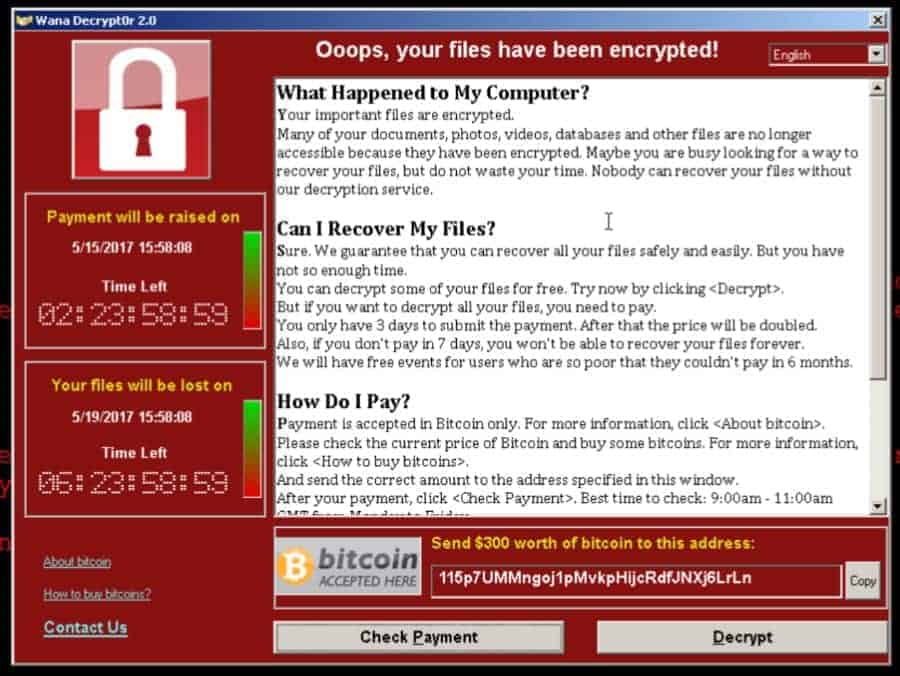
WannaCry or the Cyber-Event that should never have happened Ok, the WannaCry tears are drying and InfoSec and IT professionals around the world are catching up on sleep lost over the weekend. A fair number of them are probably, like me, wondering how this became so ugly and so widespread. While I know this cyber event had […]

